How to find someone’s IP address: Ways to know if someone is spying on your IP address
IP addresses can determine your physical location. They can do so with surprising accuracy in some cases. Advertisers and adversaries can track you online using these addresses. This can reveal your personal identifiers like phone numbers. They can also enable others against you to launch targeted attacks.
Hence it is very important that you secure your devices to avoid potential threats.
Table of Contents
How to find someone’s IP address?. 1
How to find out if someone is spying on your IP address?. 2
Use an anti-spyware software. 2
View active Internet Connections. 2
Examine your installed programs. 3
Examine Your Wi-Fi Security. 3
How to find someone’s IP address?
-
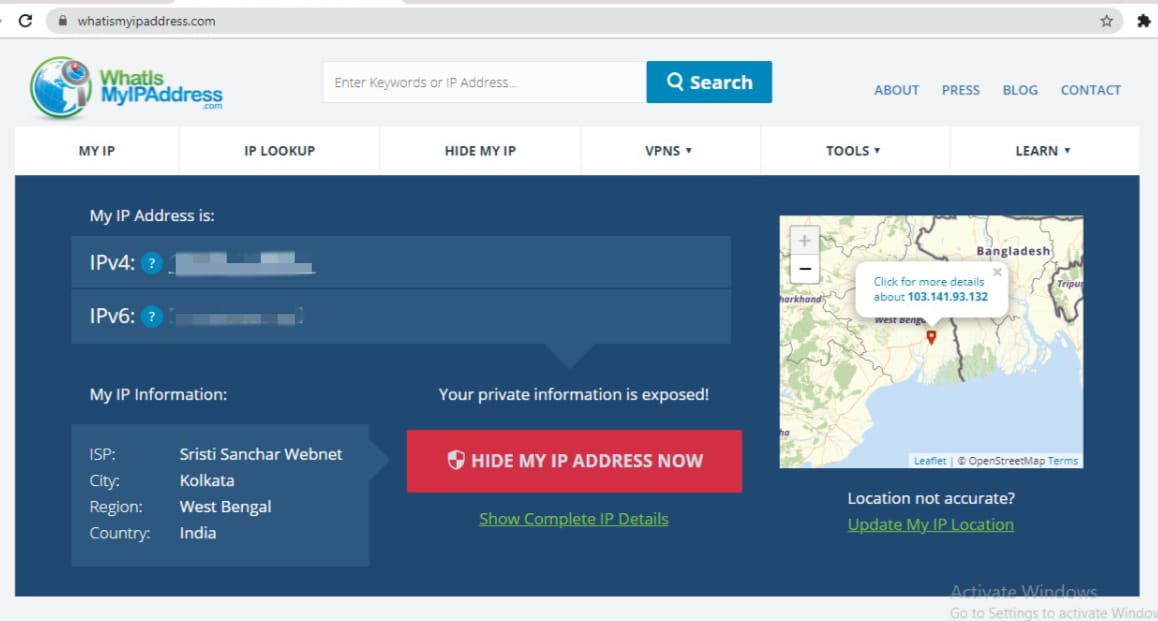
If someone uses or borrows your computer, they can quickly determine your IP address. Websites like WhatIsMyIPaddress.com. It appears right away.
- A stranger can tap into your wireless network if it isn’t sufficiently secured. Furthermore, if you allow a guest to access your network (and you provide the password), they will be aware of your IP address.
- Most internet/ email providers no longer include the IP address of the one sending an email. However, smaller ISPs or users who set up their own email server, may still be giving their IP address.
- You can reveal your IP address through the use of an HTML bug in an email. This bug is neither a virus nor a dangerous program. It is just a piece of code embedded in a picture attached to an email you received. When you view the image, the bug informs the sender that you have viewed the email along with your IP address. There are even services that assist users in setting up email bugs.
-
Social networking platforms like Facebook, Twitter, Instagram, and others do not share IP addresses between users. However, site administrators do that. They will also record your IP address if you click on an ad or link on the site.

- The use of messaging apps is rapidly increasing. Every time you use a messaging app like WhatsApp to converse with someone, your phone uses an IP address. Your IP address is invisible to the person you contact. However, the website to which you sent the message has access to your IP address if you click on a link in the message. Several websites are available that let you construct trackable links.
- Your IP address is your digital pass to connect to the internet. You leave it behind every time you visit a website. A website can examine their Web servers for all IP addresses to see how far their message has spread. They can also figure out who is a returning visitor.
- Participating in a forum to express ideas is becoming increasingly popular. Online education has vastly promoted it. Your IP address is what the administrator uses to identify your computer.
-
Bloggers write in part to hear what their readers have to say. Hence, the blog administrator can obviously read what you have written. However, with a few keystrokes, they can also find out your IP address.
Hence, it is increasingly evident that tracking or finding someone’s IP address is not at all a tough task. So, the real question is what preventive measures can you take to protect your privacy.
How to find out if someone is spying on your IP address?
There are many steps that you can take to protect your devices from intruders and attackers. Here are some of the most efficient and trustworthy measures.
Use an anti-spyware software
Installing an anti-spyware tool is one of the greatest approaches. It is also an excellent preventative precaution. They identify malware as well as a variety of other threats. They can detect unsecured network ports and camera monitoring. Most importantly, they not only identify but also actively fight these threats.
Some good recommendations for anti-spyware are:
3. Malwarebytes
5. Spybot
Each time the application detects a breach, it will notify you. The program allows you to enable a block to prevent it from happening again. In some cases the application can block it itself automatically.
We recommend that you download the free trial version of any software from the list above. For the most part, they are all free. If you want extra features you will have to pay for the full version. The trial version usually gives you a sample of the extra features.
View active Internet Connections
Viewing all active online connections your computer is the next best approach.
In Windows, TCPView is an excellent tool for this. You may examine which processes on your computer link to a given remote address. Because there could be a lot of entries here, it is better to close your browser and go offline. You can then sort the list using Remote Port.
Another tool that operates on Mac is the Wireshark packet analyzer. But its learning curve is quite steep.
Examine your installed programs
Malware is one of the most prevalent ways by which intruders track your computer. Hence, it is essential that you run a scan of the apps you have installed. Remove any apps or programs that you don’t recognize. If there are apps that you no longer use, uninstall them as soon as possible. IObit Uninstaller is one of the greatest tools for doing so.
Examine Your Wi-Fi Security
Not all Wi-Fi networks, especially public hotspots, require a password. If you’re using Wi-Fi on a laptop or desktop, make sure the network you are connecting to is safe.

This does not explicitly mean that your computer is being watched. However, it does increase the likelihood, especially if it does not require a password. Someone else on the network has a lot better chance of noticing that you have connected to it. They can monitor your wireless traffic. This will enable them to pick up things like the passwords, the photographs you post online, and so on. So check if the Wi-Fi network is open and unencrypted.
Look for any open ports
Network ports connect your computer to the internet. Ports 80, 21 and 443 are common ports for this specific purpose. However, there could be a lot more ports open. This depends on your installed programs and whether you have set up port forwarding rules.
Someone could take advantage of having a lot of ports open. They may use specific ones that you are not using to contact with your computer remotely. This way they can send viruses and access other files, passwords, images, and so on.
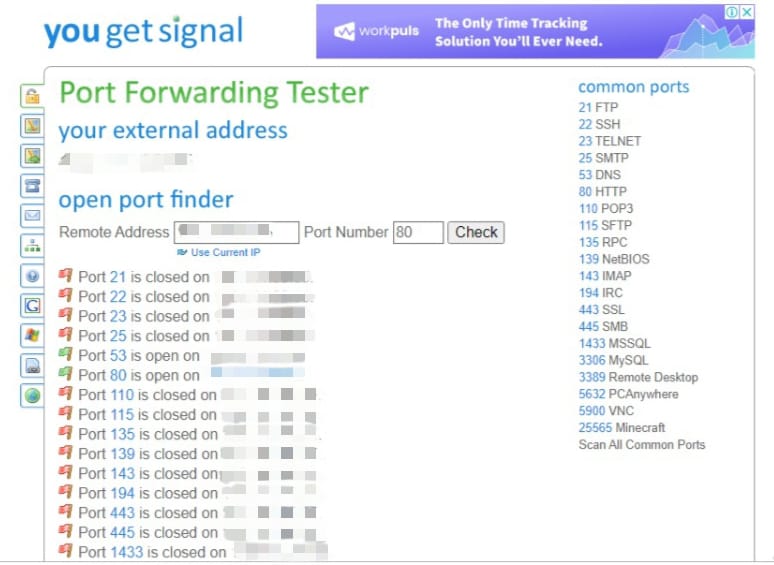
To scan the ports on your network, use a port checker like this one. You can stop ports by login into your router or by using a firewall tool to prevent them.
Do not customize Google Ad settings
The most intriguing aspect of protecting yourself online is Google’s ad settings page. Google builds a personalized profile for each of its users. This is based on their distinct interests. Various advertisements track you around the internet depending on this profile. As a result, it is critical that you leave your Google account’s ‘ad personalization’ option unchecked.
Don’t forget to take these precautionary measures for all your devices. This way you can guarantee that you are free and protected from any malicious activity online.